Analysis Report on "Second Date" Spyware: Network Attack: The Real Identity of American Personnel Related to Northwestern Polytechnical University Locked Down
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis on a "spy" software called "SecondDate". This "spy" software targets gateway device platforms such as routers based on platforms such as FreeBSD, Linux, SunSolaris, JuniperJunOS, and can achieve malicious functions such as network traffic eavesdropping, hijacking, man in the middle attack, and inserting malicious code, In order to cooperate with other "spy" software to complete complex network "spy" activities
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis on a "spy" software called "SecondDate". This "spy" software targets gateway device platforms such as routers based on platforms such as FreeBSD, Linux, SunSolaris, JuniperJunOS, and can achieve malicious functions such as network traffic eavesdropping, hijacking, man in the middle attack, and inserting malicious code, In order to cooperate with other "spy" software to complete complex network "spy" activities.
According to internal NSA documents leaked by the Shadow Broker, the malware is a network "spy" weapon developed by the National Security Agency (NSA) of the United States. The "SecondDate" spyware is a specialized tool for man in the middle attacks, typically residing on boundary devices of the target network, sniffing network traffic and hijacking or tampering with specific network sessions as needed.
During the collaboration between the National Computer Virus Emergency Response Center and 360 Company in investigating the network attack on Northwestern Polytechnical University by the National Security Agency (NSA), multiple samples of this spyware were successfully extracted and the true identities of the NSA staff behind this network "espionage" operation were identified.
The "Second Date" spyware is mainly deployed on target network boundary devices (gateways, firewalls, boundary routers, etc.), secretly monitoring network traffic, and accurately selecting specific network sessions for redirection, hijacking, and tampering as needed.
Technical analysis has found that the "SecondDate" spyware is a high-tech network espionage tool. Developers should have a deep foundation in network technology, especially familiarity with network firewall technology. It is almost equivalent to installing a set of content filtering firewalls and proxy servers on the target network device, allowing attackers to fully take over the target network device and the network traffic flowing through it, thereby achieving long-term eavesdropping on other hosts and users in the target network, and serving as a "forward base" for attacks, More cyber attack weapons can be delivered to the target network at any time.
The "Second Date" spyware resides on network boundary devices such as gateways, boundary routers, and firewalls for a long time, and can accurately filter and automatically hijack massive data traffic, achieving a man in the middle attack function. Its main functions include network traffic sniffing, network session tracking, traffic redirection hijacking, traffic tampering, and so on.
This "spy" software targets network device platforms such as routers and firewalls. SecondDate supports distributed deployment and consists of server-side programs and client programs. Attackers implant client programs into target network devices through other means in advance, and then use server-side programs to command and control the client. The main workflow and technical analysis results are as follows:
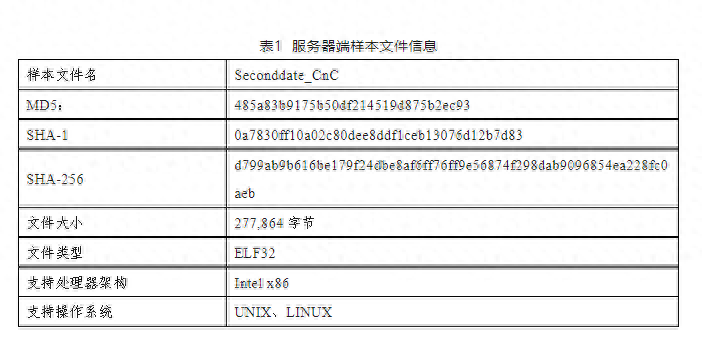
The main function of the server is to establish a connection with the client and issue control rules, allowing the client to complete corresponding malicious operations. As shown in Table 1, Figure 1, Figure 2, and Figure 3.
1. Connecting clients
Establish a connection with the client by specifying the client IP and port number in the command line parameters.

Figure 1 Establishing a connection with the client
2. Obtain the current status of the client

Figure 2 Obtaining Client Status Information
3. Configure client rules

Figure 3 Configuring Client Rules
As shown in Figure 3, attackers can filter network traffic by specifying source IP address, source port, destination IP address, destination port, protocol type, TCP flag, etc. They can also specify matching regular expression files to obtain traffic with specific content, and can insert files containing specific content into the traffic.
From the analysis results, it can be seen that after the client is implanted and configured with corresponding rules, it can run silently in the background of network devices. Attackers can use the server side for control or directly log in to the background of network devices for command control. As shown in Table 2, Figure 4, Figure 5, and Figure 6.

1. Specify local port

Figure 4: Client specified local port
2. Perform corresponding actions according to instruction rules

Figure 5 Client Execution Control Instructions
3. Insert File

Figure 6 Client Execution File Insertion Instruction
4. Instruction set
After analysis, the main instructions supported by the client and their functional descriptions are shown in Table 3.

The client instruction set is very rich, which can achieve malicious operations such as content filtering, middleman hijacking, and content injection of network traffic.
The 'SecondDate' spyware supports running on various operating systems such as Linux, FreeBSD, Solaris, JunOS, and is compatible with multiple architectures such as i386, x86, x64, SPARC, and has a wide range of applications.
SecondDate spyware is typically used in conjunction with various network device vulnerability attack tools targeting firewalls and routers in specific intrusion action offices (TAOs). After successful vulnerability attacks and obtaining corresponding permissions, it is implanted into the target device.
The "Second Date" spyware is divided into a server and a control end. The server end is deployed on the target network boundary device and monitors and filters all traffic in real-time through the underlying driver; After the control end triggers the activation mechanism by sending a specially constructed data packet, the service end parses the reconnection IP address from the activation packet and actively reconnects. The network connection uses UDP protocol, with encrypted communication throughout the entire process and random communication ports. The control end can remotely configure the working mode and hijacking target of the server, and select any target within the network to carry out a man in the middle attack according to actual needs.
We carried out technical investigations with our industry partners around the world. After tracing back to the source layer by layer, we found that thousands of network devices all over the world were still secretly running "second date" spyware and its derivatives, and found that springboard servers remotely controlled by the National Security Agency (NSA), most of which were distributed in Germany, Japan, South Korea, India and Taiwan, China, China. With the joint efforts of our industry partners from multiple countries, we have made significant breakthroughs in our work and have successfully identified the true identities of the National Security Agency (NSA) personnel who launched a cyber attack on Northwestern Polytechnical University.
With the continuous enhancement of China's comprehensive national strength and profound changes in the international strategic landscape, overseas "spy" intelligence agencies are increasing their efforts to carry out espionage and intelligence activities in China. Carrying out "spy" and secret theft activities through the internet has become one of the main means.
In this context, the Chinese government, industry leading enterprises, universities, medical institutions, research institutions, etc. should accelerate the investigation of their own network "spy" attack clues and security risks, cooperate with capable network security companies to obtain digital security services, rely on big data, platforms, probes, and experts to build a security operation center, and obtain digital security capabilities at low cost and high efficiency. Realize the "visibility" of all network assets, network situation, and national level espionage attacks, with core security capabilities such as "handling" security risks, advanced threats, and espionage operations. Ultimately, it can analyze, discover, block, clean, and recover in real-time.
New evidence! The mysterious hacker identity of the Cyberattack Western Polytechnic University has been locked down, and "spyware" is the key!
Disclaimer: The content of this article is sourced from the internet. The copyright of the text, images, and other materials belongs to the original author. The platform reprints the materials for the purpose of conveying more information. The content of the article is for reference and learning only, and should not be used for commercial purposes. If it infringes on your legitimate rights and interests, please contact us promptly and we will handle it as soon as possible! We respect copyright and are committed to protecting it. Thank you for sharing.(Email:[email protected])