Will the Physical ID Card Become a Thing of the Past? "Black Technology" Brings an Identity Revolution, How Should the Elderly Cope?
Will the Physical ID Card Become a Thing of the Past? "Black Technology" Brings an Identity Revolution, How Should the Elderly Cope?The second-generation ID card has become an integral part of our daily lives, but now news is emerging that it may be discontinued soon. Replacing it is an astonishing "black technology" that will fundamentally change the way we verify our identities...
Gui Haichao: The only astronaut without military status, with a young and beautiful wife and a special identity
Before reading this article, please kindly click on 'Follow', which not only facilitates your discussion and sharing, but also brings you a different sense of participation. Thank you for your support!Wen | UenoEditor | Fang WenYesterday, the Shenzhou 16 manned spacecraft landed smoothly...
Exposure of Xianyu's "Another Identity": Pornographic transactions are rampant and can be directly "door-to-door service"
Xianyu is a second-hand trading platform, but recently it has been exposed that there is a problem of rampant pornography trading, and even sparked discussions about "door-to-door services". This issue is not only an impact on the image of the Xianyu platform, but also involves challenges in social governance and network regulation...
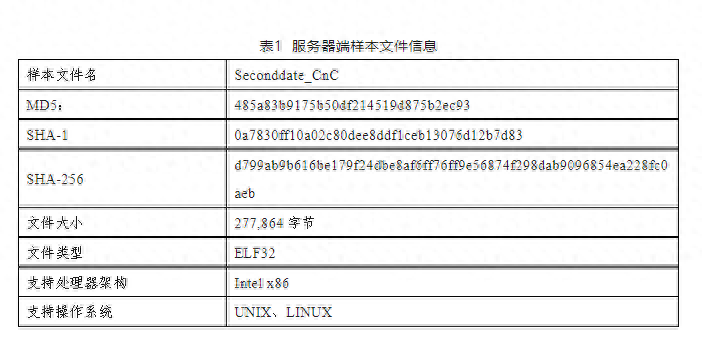
Analysis Report on "Second Date" Spyware: Network Attack: The Real Identity of American Personnel Related to Northwestern Polytechnical University Locked Down
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis on a "spy" software called "SecondDate". This "spy" software targets gateway device platforms such as routers based on platforms such as FreeBSD, Linux, SunSolaris, JuniperJunOS, and can achieve malicious functions such as network traffic eavesdropping, hijacking, man in the middle attack, and inserting malicious code, In order to cooperate with other "spy" software to complete complex network "spy" activities...
New evidence! Mysterious Hacker Identity Locked Out for Cyberattack at Western Polytechnic University
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis of a spy software called "Second Date". The analysis report shows that the software is a network spy weapon developed by the National Security Agency (NSA) of the United States...
Saudi Arabia | Starting from October 1st, mobile phones will display the name and identity of the caller
Previously, the Saudi Committee on Communications, Space and Technology (CST) submitted a draft technical specification for displaying the names and identities of mobile phone callers, which will take effect on October 1, 2023.The name and number of the calling party must be displayed in the call log, and the mobile device must be able to receive and display the names and numbers of callers of all technology types (including 2G, 3G, 4G, and 5G)...