Arctic Sea Ice Flows South: Northwest Passage Navigation Season Shortens, Safety Risks Increase
Arctic Sea Ice Flows South: Northwest Passage Navigation Season Shortens, Safety Risks IncreaseIn recent years, the accelerating melting of Arctic sea ice due to global climate change has not only raised concerns about rising sea levels and ecological changes but also brought new challenges to the safety of navigation in the Northwest Passage. A new study has found that from 2007 to 2021, the amount of thick sea ice flowing south from the Arctic Ocean has increased, resulting in a shorter ice-free navigation season in some parts of the Northwest Passage and increased risks to navigation safety...
The 2023 Huawei Cloud Northwest Rendering Center Ecological Conference was successfully held in Qingyang, Gansu
On November 3rd, the 2023 Huawei Cloud Northwest Rendering Center Ecological Conference with the theme of "Cloud Gathering Ecology, Digital Projection of the Future" was successfully held in Qingyang City, Gansu Province. As a stop in the Huawei Cloud's "Hundred Cities, Ten Thousand Enterprises Travel to China" special action, this conference revolves around digital transformation, discusses new opportunities for the "East Digital and West Computing" project, and explores innovative paths for the development of Qingyang's digital economy and rendering industry...
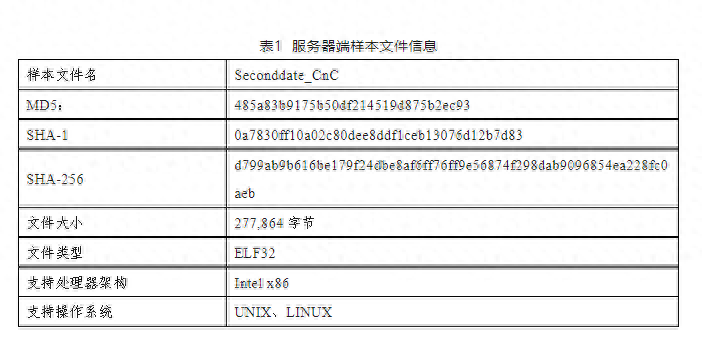
Analysis Report on "Second Date" Spyware: Network Attack: The Real Identity of American Personnel Related to Northwestern Polytechnical University Locked Down
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis on a "spy" software called "SecondDate". This "spy" software targets gateway device platforms such as routers based on platforms such as FreeBSD, Linux, SunSolaris, JuniperJunOS, and can achieve malicious functions such as network traffic eavesdropping, hijacking, man in the middle attack, and inserting malicious code, In order to cooperate with other "spy" software to complete complex network "spy" activities...