At 3:30 AM, Deepseek servers suffered a saturation attack from US hackers!
At 3:30 AM, Deepseek servers suffered a saturation attack from US hackers!At 3:30 AM, while most people were asleep, the world's leading "technological power" launched a massive saturation attack on Deepseek servers, which had just topped app store charts in multiple regions. The precise timing clearly indicates meticulous planning...
34-Year-Old Young Scientist Li Haizeng Passes Away Due to Sudden Heart Attack, Triggering Public Mourning and Concerns about Heart Attacks
34-Year-Old Young Scientist Li Haizeng Passes Away Due to Sudden Heart Attack, Triggering Public Mourning and Concerns about Heart AttacksAccording to The Paper news on September 8th, Professor Li Haizeng, a renowned young scientist, professor, and doctoral supervisor of the School of Energy and Power Engineering at Shandong University, passed away in Qingdao on August 29th, 2024, due to sudden heart attack. He was 34 years old...
Foxconn Terry Gou counterattacks! What is your intention to announce the cancellation of all overtime after clarifying the rumors?
Foxconn was previously exposed to investigation by two major departments. Firstly, the tax department conducted tax inspections on its enterprises in Guangdong and Jiangsu; Secondly, the Ministry of Natural Resources conducted on-site investigations on Foxconn's land use in Henan, Hubei, and other areas...
India investigates whether opposition party figures' iPhones have been attacked by 'hackers'
Indian Minister of Railways, Communications, Electronics and Information Technology Ashvini Vaishnau said on the 2nd that India's cybersecurity department is investigating complaints from senior opposition figures that some of their phones have been "hacked". These people received warning messages from Apple in the United States...
India finally faced a counterattack, and Xiaomi launched a counterattack. However, Indian media said please understand our grievances
India has always been known as the destination for foreign enterprises. No foreign enterprise can achieve a complete withdrawal in India...
The time has come for a joint counterattack! After being unable to evacuate India, India has once again "harvested" Chinese enterprises!
India seems to have bitten down Chinese companies.In the past, international giants such as Nokia, Samsung, IBM, and Google have all faced huge fines in the Indian market, including our Chinese enterprises...
Attack the "Little Giant" | Visual Bits: Give the production line a pair of "smart eyes" and install a "smart brain"
Editor's note:There is a group of enterprises, small in size, but ambitious, possessing unique skills, and wandering the world alone, known as the "little giants". In Changsha, the "little giants" are like stars and moons, deeply cultivating their respective fields and running dark horses in the industry, becoming a dazzling light in the high-quality development of the city's industrial economy...
A ransom of 51 million US dollars! Johnson Controls was attacked by ransomware, resulting in partial operational interruption
Johnson Controls International suffered from a so-called large-scale ransomware attack that encrypted many of the company's devices, including VMWareESXi servers, affecting the operations of the company and its subsidiaries. Johnson Controls is a global leader in the field of intelligent buildings, committed to creating safe, healthy, and sustainable spaces with a history of over 140 years...
Actor Liu Jin angrily attacked iPhone rights at the entrance of an Apple store and starred in "Charlotte's Troubles"
On September 17th, actor Liu Jin posted a statement video on his personal social account. Replay suspend 00:04 / 01:32 direct seeding 00:00 Enter full screen 0 Click and hold to drag videos TransparencySource: Phoenix NewsIn the video, Liu Jin recounts the dispute he had with Apple's after-sales service and angrily smashed his iPhone 13 ProMax at the entrance of the Apple store in Wangfujing...
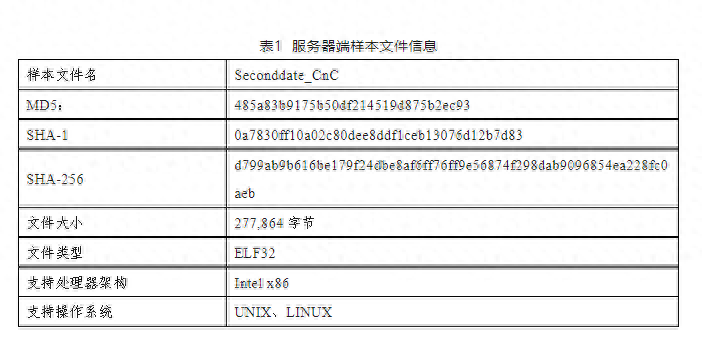
Analysis Report on "Second Date" Spyware: Network Attack: The Real Identity of American Personnel Related to Northwestern Polytechnical University Locked Down
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis on a "spy" software called "SecondDate". This "spy" software targets gateway device platforms such as routers based on platforms such as FreeBSD, Linux, SunSolaris, JuniperJunOS, and can achieve malicious functions such as network traffic eavesdropping, hijacking, man in the middle attack, and inserting malicious code, In order to cooperate with other "spy" software to complete complex network "spy" activities...
New evidence! Mysterious Hacker Identity Locked Out for Cyberattack at Western Polytechnic University
Recently, the National Computer Virus Emergency Response Center and 360 Company conducted a technical analysis of a spy software called "Second Date". The analysis report shows that the software is a network spy weapon developed by the National Security Agency (NSA) of the United States...
Typhoon "Dussuri" Attacks Ningbo Coastal Waters and Enters Level IV Typhoon Protection
Ningbo, China Central Radio Network, July 23 (reporter Yu Ye, correspondent Zhang Jie) At 11:00 on July 23, the 5th typhoon of this year, "Du Surui", was located at 14.8 degrees north latitude and 128...